Phishing 301: Targeted Phishing Attacks
January 13, 2014 | Authored by William Prohn CISSP, CISA, CGEIT, CRISC
It seems that criminals and online attackers are constantly finding new, and ever more clever methods for stealing information, always staying one step ahead of the law. What can you do to protect yourself in this war against cybercrime? To start, you must increase your awareness of the threats that face you on a daily basis.
Targeted Schemes
Targeted Schemes, otherwise referred to as ‘spear phishing’ attacks, are likely to become a top concern of security professionals for 2014 due to their above average rate of success. Spear phishing derives its name from the personal information used by attackers to craft highly focused phishing emails (targeting, or ‘spearing,’ a specific individual). In many cases, targeted phishing schemes use publicly available information from social media or company websites to draft emails that become so believable as to be almost impossible to avoid. Luckily, there are still some straightforward steps you can take to protect yourself from these targeted phishing schemes.
It is always recommended that you mouse-over links contained in an email, regardless of the apparent sender. Once you have made this a habit, you will be more likely to catch a spear phishing attack that is relying on your implicit trust of the email’s origin. Avoiding .zip and .exe attachments is another habit that should be formed, regardless of the sender. If you receive a file unexpectedly from a friend, relative or co-worker, take the extra second to fire back an email confirming the legitimacy of the file. Any email that is requesting you to ‘verify,’ ‘confirm’ or otherwise enter a set of credentials should be immediately treated as a dangerous phishing attack.
It’s important to consider just how much information we post on social networks and company websites. Imagine putting together your own spear phishing attack, based on only publicly available information. For most individuals, that could include: recent events (birthdays, company parties, vacations), names of family/friends/colleagues, professional titles/departments (emails from the CEO of your company), schools and family institutions (emails from teachers or principles), and many other pieces of very personal information. Let’s consider the following email: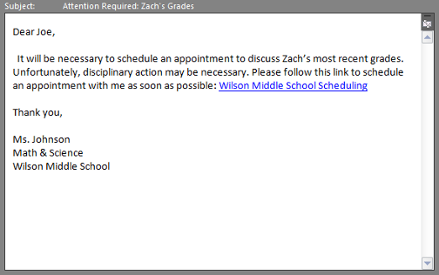
Let’s assume that Joe is the CEO of a large local manufacturing company. He could have been chosen for this attack by identifying his important title and work email address on LinkedIn or his company’s website. Next, the attackers simply perform a Facebook search and discover that Joe here has a child, Zach, in middle school. Joe likes to post pictures and updates about his kids, including the recent pageant at Zach’s school, Wilson Middle School. After performing the previous tasks (and taking no more than a few minutes to do so), the phishers Google: “Wilson Middle School,” and select Zach’s math teacher from the list of staff and faculty. At this point, the attackers have all the information necessary to craft the spear phish seen above and gain access to ‘Joe the CEO’s’ computer.
How many parents would ignore an email such as this? Even if the rate of success was only 50%, the minimal time spent developing this attack makes it incredibly efficient and effective for cyber criminals. If a parent took the 1 second necessary to mouse-over the link in the phishing email, they would discover that the address is not Wilson Middle’s Scheduling service, but instead malicious software.
Again, while the nature of these attacks are incredibly personal, if you practice good security habits you will dramatically increase your chances of avoiding an email scam.
Checklist
Consider printing out the checklist below to help you identify phishing emails and protect your private information.

For more information, please contact William Prohn at wprohn@dopkins.com.

About the Author
William Prohn CISSP, CISA, CGEIT, CRISC
Bill oversees all aspects of information technology for the firm, and provides consulting services to a wide spectrum of Dopkins’ clients. He has over 30 years of experience in accounting and business information systems. His specific interests include creating meaningful, practical management information using computer technologies, and the security of business information and systems.

