Phishing 201: Advanced Phishing Threats
January 8, 2014 | Authored by William Prohn CISSP, CISA, CGEIT, CRISC
It seems that criminals and online attackers are constantly finding new, and ever more clever methods for stealing information, always staying one step ahead of the law. What can you do to protect yourself in this war against cybercrime? To start, you must increase your awareness of the threats that face you on a daily basis.
Phishing 101: What’s a ‘Phish’ Anyway? introduced you to email threats such as the “Nigerian Letter Scam.” In our second phishing post, we’re going to cover scams that are considerably more complex than the classic Nigerian scam. As computer users have become more aware, and security technology more advanced, cyber criminals have been forced to try and imitate trusted companies in order to lure in their victims. Below, you will find a few examples of these scams so that you can be better armed the next time an attacker strikes.
Advanced Schemes
Cyber-attacks typically fall in to one of two categories: opportunistic or targeted. Opportunistic attacks rely on the probability that at least one user (out of potentially thousands) will fall victim to the attack, with no regard for the identity of that individual. Targeted attacks, which will be covered in Part 3 of this blog, seek out specific users who have been selected in advance for possessing some value to the attacker.
With advanced phishing schemes, impersonation is the name of the game. Attackers have been crafting incredibly accurate emails that appear to be coming from legitimate businesses, sometimes even mimicking an individual’s employer.
Let’s take a look at some common examples of advanced phishing emails:
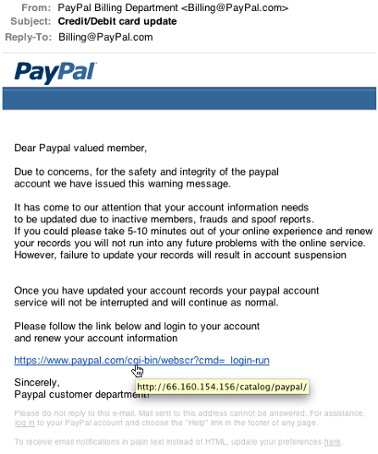 At first glance, this email appears legitimate. The email address “Billing@PayPal.com” aligns with what we might expect to see from PayPal’s Billing Department. “Credit/Debit card update,” the subject line of the email, may raise concern if not expected, but is not in and of itself a red flag. Now, when we begin to read the body of the email we note our first red flag: “Dear Paypal valued member.” If this email were coming from PayPal’s billing department, and is in reference to your credit/debit card information, wouldn’t you expect them to address you by name? We’ll consider that strike one.
At first glance, this email appears legitimate. The email address “Billing@PayPal.com” aligns with what we might expect to see from PayPal’s Billing Department. “Credit/Debit card update,” the subject line of the email, may raise concern if not expected, but is not in and of itself a red flag. Now, when we begin to read the body of the email we note our first red flag: “Dear Paypal valued member.” If this email were coming from PayPal’s billing department, and is in reference to your credit/debit card information, wouldn’t you expect them to address you by name? We’ll consider that strike one.
The use of the English language in the first paragraph is enough to make you stop reading right then and there, but more importantly acts as a clear indicator that this email is fraudulent. Improper grammar and the failure to use specific identifiers (such as your name or account number) are found in the remaining paragraphs and will be counted collectively as strike two for this email.
The image above illustrates the use of the “mouse-over” technique, in which the user simply hovers their mouse over a link without clicking. The result is that the true destination of the link is displayed. If the link is valid, both the link and its mouse-over description should match. In this example, we see that not only do the two addresses not match; the address highlighted in yellow is indecipherable. ‘Mousing-over’ links is a critical security step that should be performed every time you click a link. For our PayPal example, this mysterious link serves as strike three. Unfortunately, this isn’t baseball, and it only takes one strike to strike out. If you think you’ve spotted a red flag, take precautions and avoid clicking links.
This email contains additional red flags that while less conclusive, may assist you in avoiding a scam. The inconsistent capitalization of the trademarked ‘PayPal’ is unusual for such a large oganization; the sender’s address identifies the PayPal Billing Department, but the body of the email specifies the ‘customer department;’ the use of the terms ‘spoof’ and ‘fraud’ are intended to throw you off the scent of this scam.
The rule of thumb here is: legitimate organizations will never ask for your username, password or other confidential information. If the email appears reasonable, and you wish to confirm the information provided within it, log in to the organization’s website through your browser (not through links contained in the email). In the above example, you could log in to PayPal’s website to confirm whether your information needs to be updated. You are advised to never reply to a similar email with confidential information, or follow a link in a similar email requesting credentials.
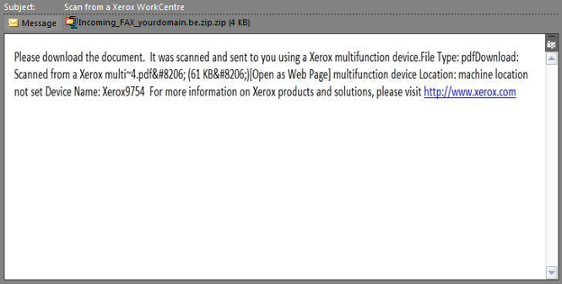
Xerox WorkCentre
The above scam has been circulating rapidly as of late, and contains a few tricks that set it apart from the rest of the field. First off, unlike the PayPal scam which appears to come from an outside party, the Xerox scam typically appears to come from within the organization that you work for. For example, instances have been seen with the following addresses: SCANS @ [YourCompany].com, XeroxWorkCentre @ [YourCompany].com, info @ [YourCompany].com and many others. Do not simply trust an email because it appears to originate from within your organization. Always vet the email against additional criteria.
Likely the biggest red flag of this email is the attached .zip file. It is a best practice to never open a .zip file that is attached to an email (that goes for .exe files as well). Many security professionals are recommending that email attachments be avoided altogether, due to the increased risk of malicious software being contained within them. Next, the body of the message provides no further detail to identify what this apparent “fax” or “scan” is. There appears to be a contradiction between the subject and the body of this email, with one referring to the file as a scan, and the other making reference to a fax. They certainly aren’t the same thing, and the contradiction seems unusual coming from what appears to be an automated system.
Whether or not you expected to receive a scan/fax, always confirm them before opening any attachments. Again, .zip files and .exe files should be avoided in all circumstances. In this case, using the mouse-over technique discussed earlier would have identified the malicious link, which was certainly not www.xerox.com!. With Advanced Scheme phishing attacks it is important to be especially skeptical. As Ronald Reagan put it: “Trust, but Verify.”
 Need Help?
Need Help?
If you are unsure that your business is adequately protected, our Information Security Baseline Review is an ideal starting point for answering all of your questions, and providing you and your key managers with a basic education of both the threats your company’s information faces and what practical approaches you can take to protect it.
Make sure to look for the final part of our phishing blog, 301: Targeted Schemes.
Remember, a false sense of security is worse than being unsure. We have a variety of tools and resources to help you. I encourage you to call to take proactive action.
For more information, please contact William Prohn at wprohn@dopkins.com.

About the Author
William Prohn CISSP, CISA, CGEIT, CRISC
Bill oversees all aspects of information technology for the firm, and provides consulting services to a wide spectrum of Dopkins’ clients. He has over 30 years of experience in accounting and business information systems. His specific interests include creating meaningful, practical management information using computer technologies, and the security of business information and systems.

